Analysis Process
Project Objective
This project followed the scenario described below:
"A friend has come to you after inheriting her sister’s computer. After using it for just one day, she has already lost some data and suspects there may be security problems with the computer. She feels that if she does any more work on the computer, it will be like walking into a trap!"
Plan of Action
- Check and secure firewall rules
- Run antivirus
- Find suspicious processes and trace these back to malicious files
- End suspicious processes
- Permanently delete suspicious files including suspicious downloads
- Recover lost/deleted user files (in this case in the Recycle Bin)
Cybersecurity Lifecycle
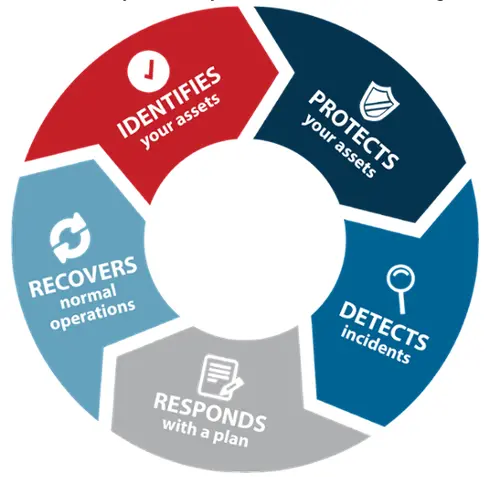
Protecting the Computer Using Proactive Protection Measures
The scenario described that data was lost due to potential malware from a previous user, the current user's sister. This malware was likely downloaded from the internet, so the firewall should be checked.
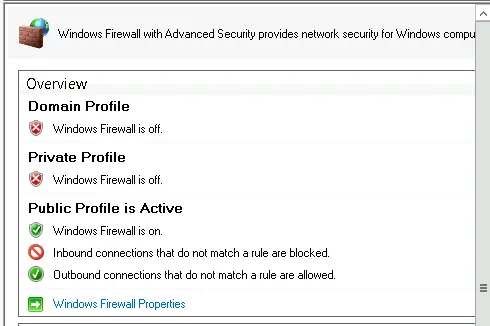
Indeed, the firewall is off, so I turned it on to block unwanted network traffic and close unnecessary ports.
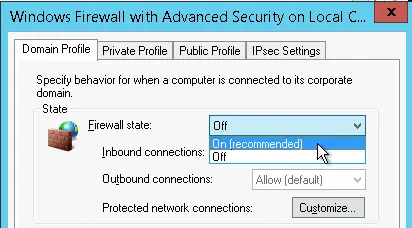
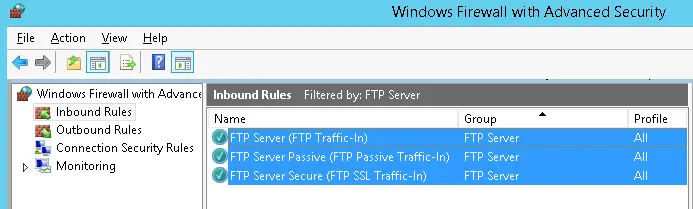
Files downloaded from the internet use FTP (File Transfer Protocol) or FTPS (File Transfer Protocol Secure). We should disable FTP as FTPS is preferred since FTPS is encrypted through SSL while FTP is unencrypted and can cause files to be read and altered during transit. As seen in the screenshot below, FTP (running on ports 20 and 21) was enabled, which I disabled so only FTPS can be utilized. FTPS runs on ports 990 and 989.
Detecting Security Problems
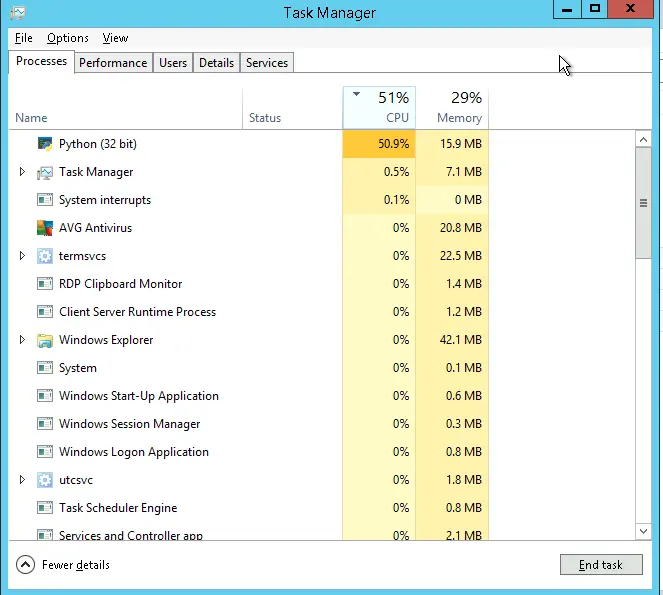
Malware can often be identified using the Task Manager. In the Task Manager, Python was using over 50% of the CPU. I decided to investigate further by choosing the "Details" tab.
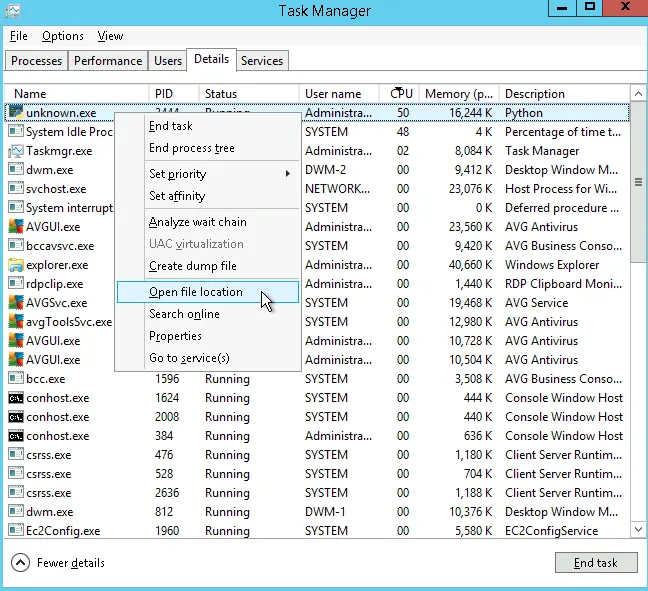
Under the "Details" tab, I found that a process titled "unknown.exe" was responsible for the high CPU usage. I opened the file location.
When I opened the file location, nothing was visible. This occurs since Windows hides hidden items by default, so I made them visible.
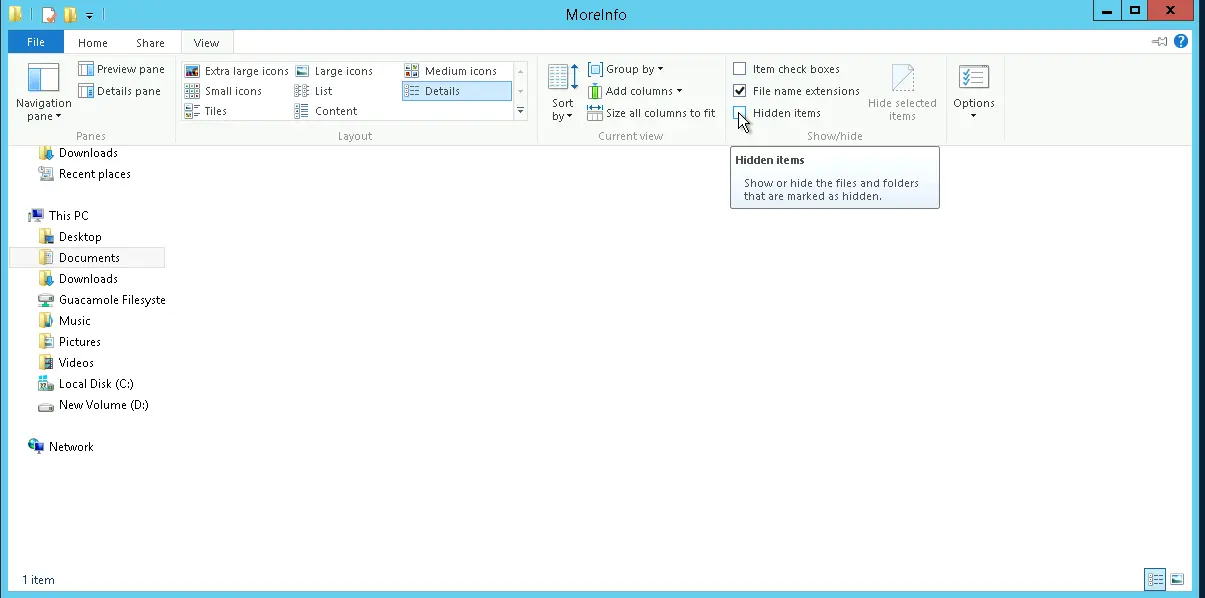
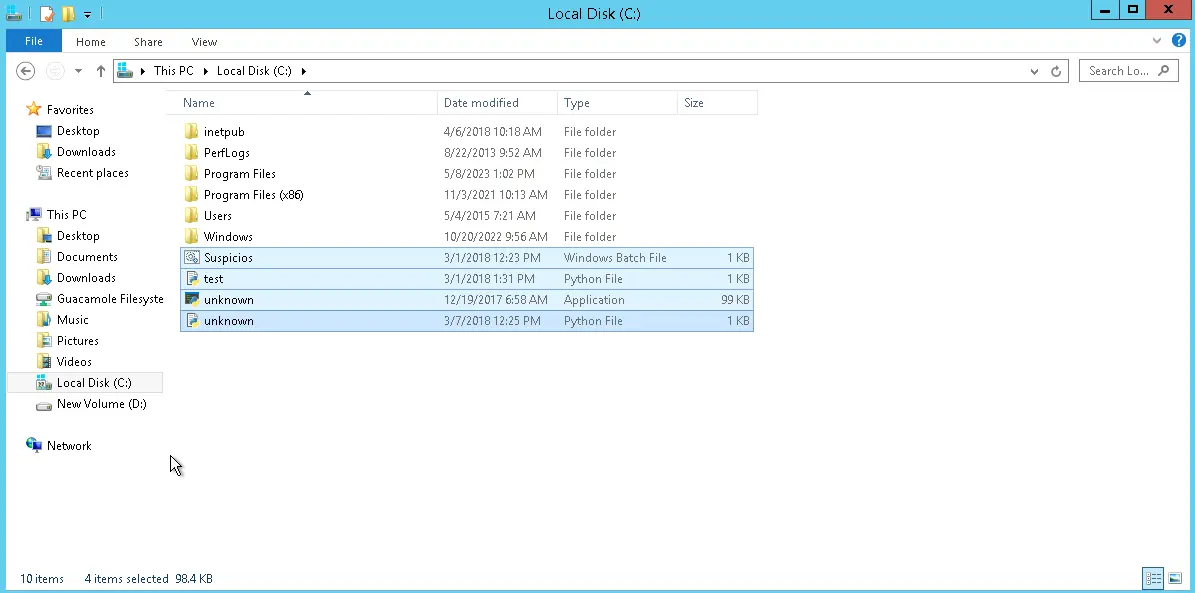
By showing hidden files, I was able to see multiple files:
- unknown.exe - the process malware file
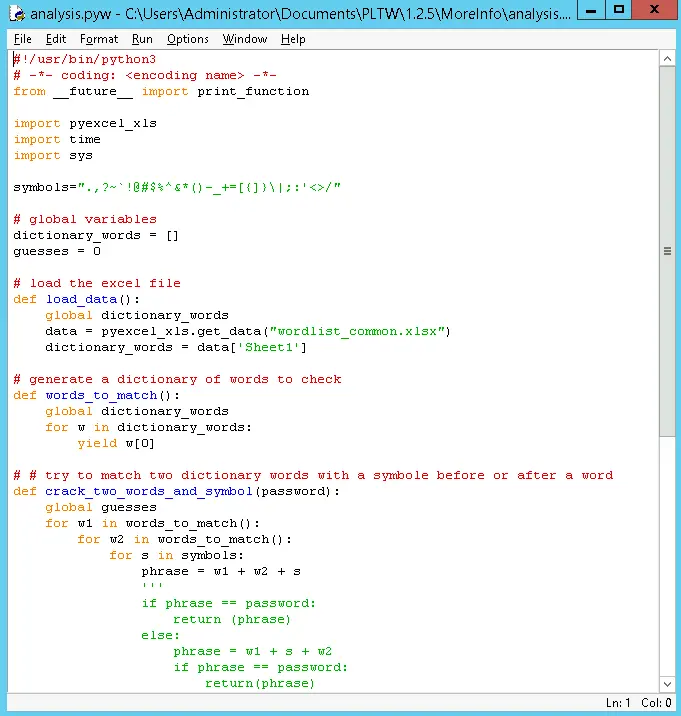
- analysis.pyw - a password cracking script
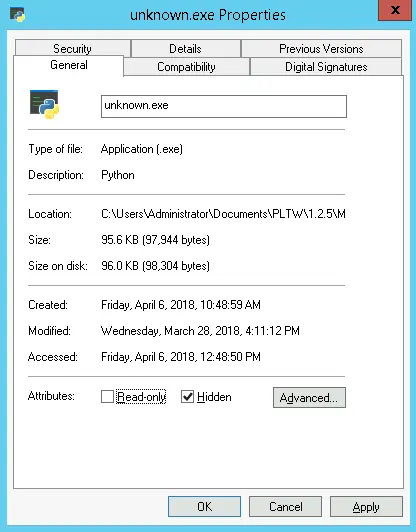
Under further analysis, unknown.exe is a renamed Python installation, and also has the digital signature of the Python Software Foundation. Unknown.exe seems to have been downloaded Friday, April 6, 2018.
Additionally, the analysis.pyw seems to be a password cracking file, so seemingly malware.
I also looked at the C:\ drive as malware often resides there. Seeing four additional suspicious files, I decided to permanently delete them.
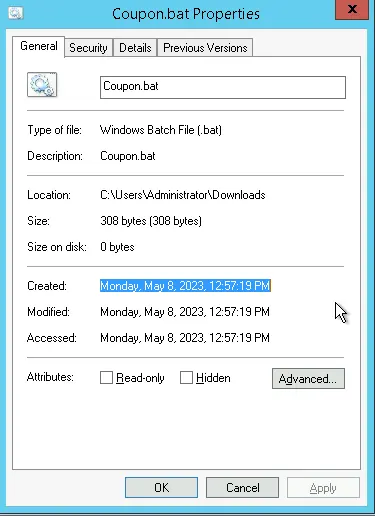
In the Downloads\ folder, I found a file named "Coupon.bat". This file runs a script in the command line, and was likely a trojan (type of malware that pretends to be legitimate). When viewing the file's properties, I determined that the malware was downloaded on May 8, 2023. This is after the unknown.exe file was downloaded, so there was likely malware before the coupon was downloaded.
If file extensions are not visible, then "Coupon.bat" would only read "Coupon", so it would seem more legitimate.
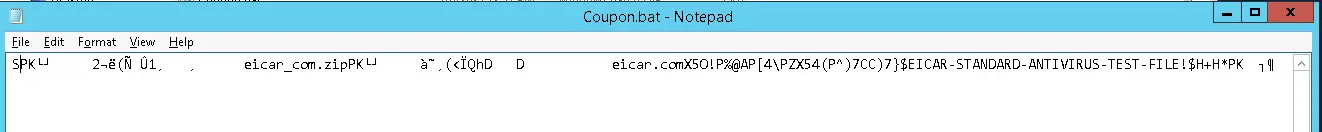
When viewing the Coupon.bat file (without running it) in a text editor, I saw the following string:
"EICAR-STANDARD-ANTIVIRUS-TEST-FILE!
After a little research, I found that EICAR is the European Institute for Computer Anti-Virus Research. This lead me to conclude that Coupon.bat was a test file for antivirus applications and not actual malware.
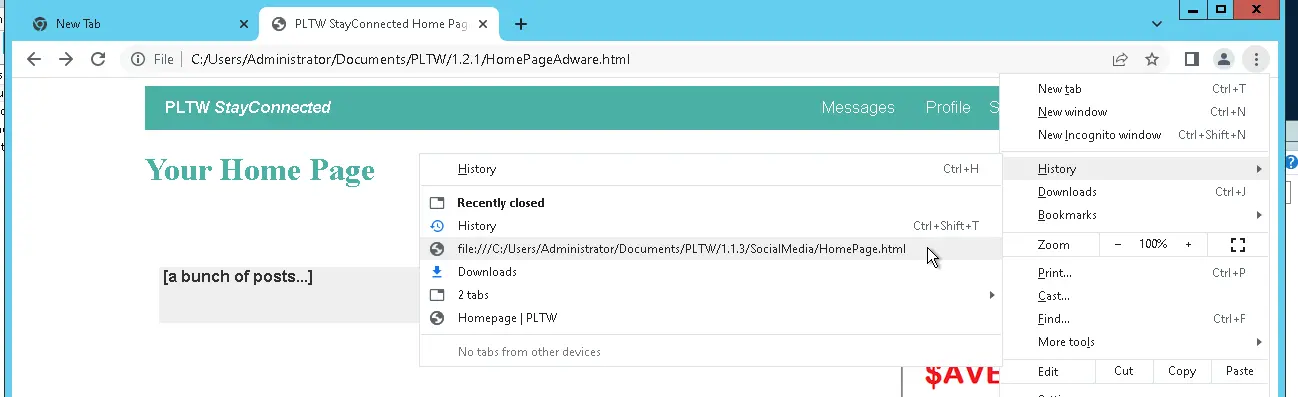
Next, I decided to find the source of the malware file, "Coupon.bat". I checked the Google Chrome browsing history, and found a single website pointing to a website with an advertisement. The advertisement reads, "FREE PRINTABLE COUPON$." This was the source of the attack.

I also ran AVG antivirus software, but it found no malware, so I think the "malware" is either just a test (this is confirmed by the EICAR statement within Coupon.bat), or the antivirus is not functioning properly.
Responding to the Problem By Removing Malicious Files and Processes
Once I had found all of the malware and traced it back to its source, I could remove all of the processes and malware.
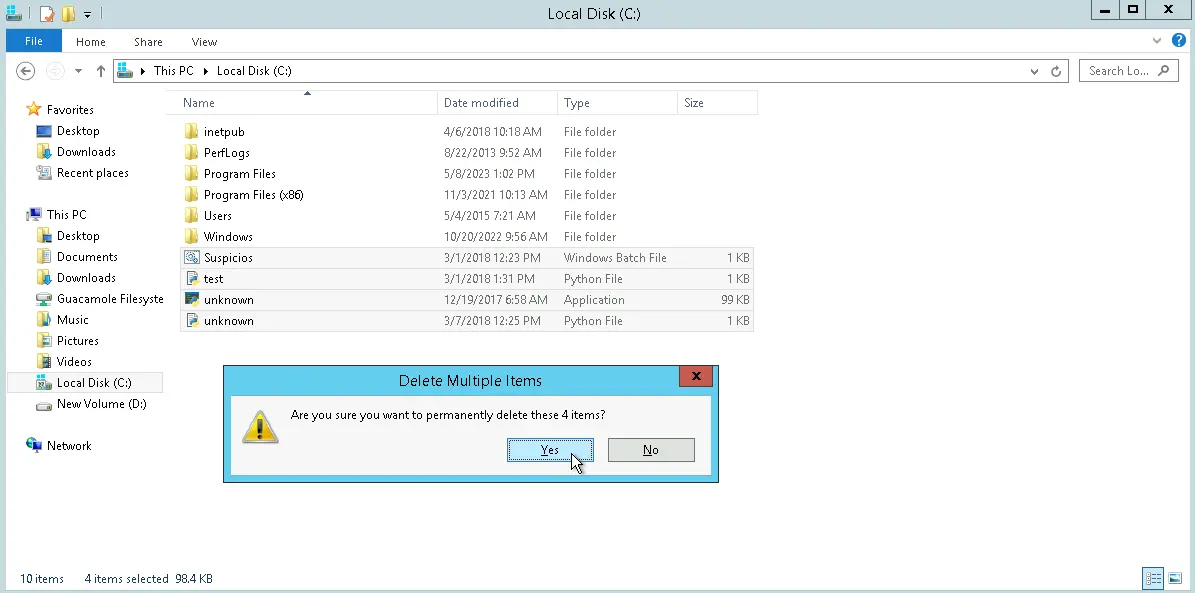
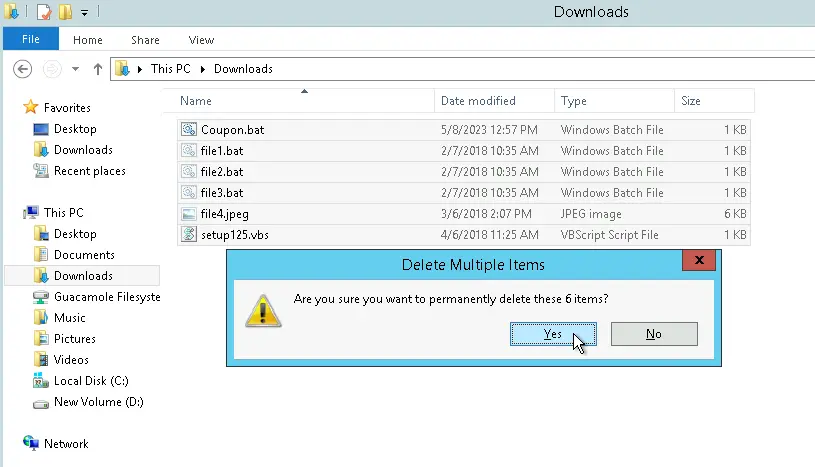
I used "Shift + Delete" to permanently delete the malware on both the C:\ drive and in the Downloads\ folder.
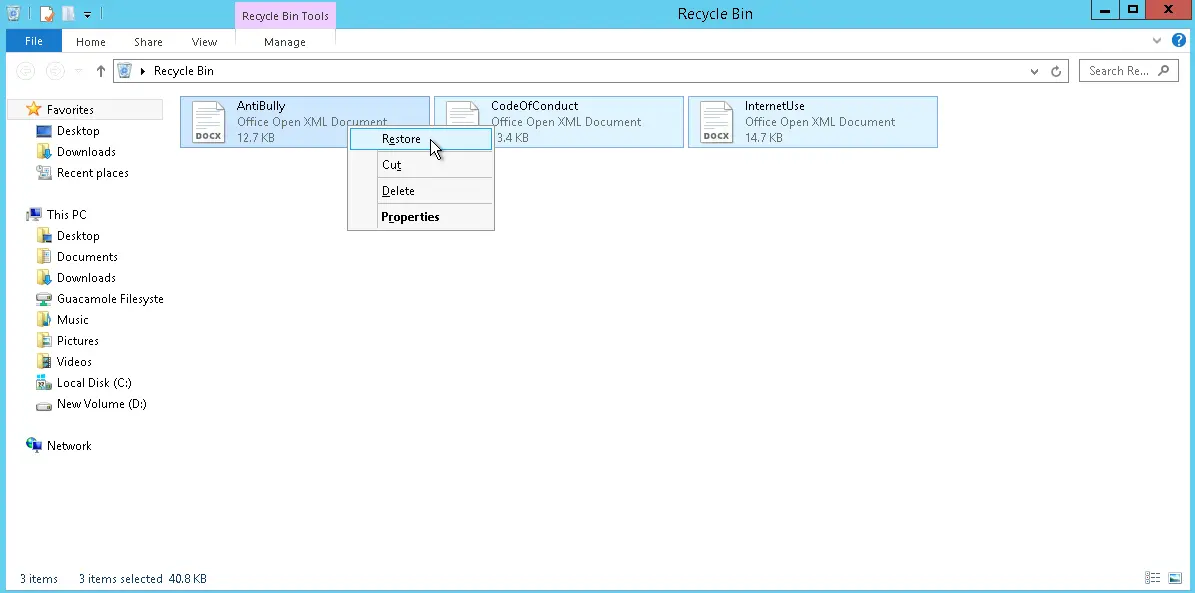
Recovering Deleted Data
The last step of the cybersecurity process was to restore the system to its previous state. A full-system backup would have been better as permanently deleted files would be recovered easily, but no backups were available. For the purpose of this lab, "deleted" files were only placed in the Recycle Bin. I restored these to the Desktop\ folder, which is where they originally were.